Microsoft On Premise Exchange Hack
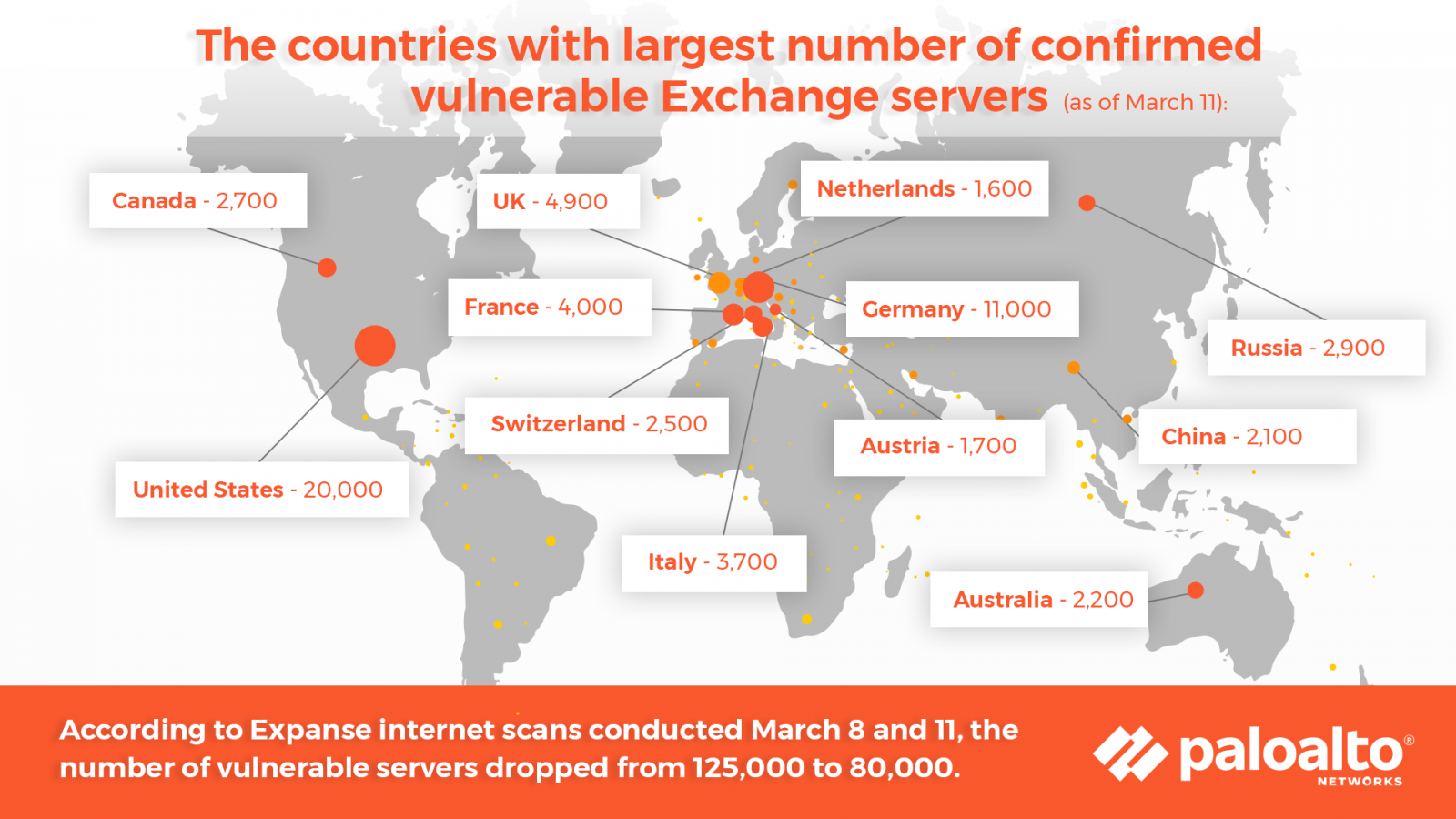
Last week Microsoft announced that the on-premises version of its widely used email and calendaring product Exchange had several previously undisclosed security flaws. The Microsoft Exchange attacks could be a lot worse than initially thought as reports suggest hundreds of thousands servers have now been hacked globally.
 Hafnium Targets Microsoft Exchange Zero Day Vulnerabilities
Hafnium Targets Microsoft Exchange Zero Day Vulnerabilities
Background of Microsoft Exchange Server hack.

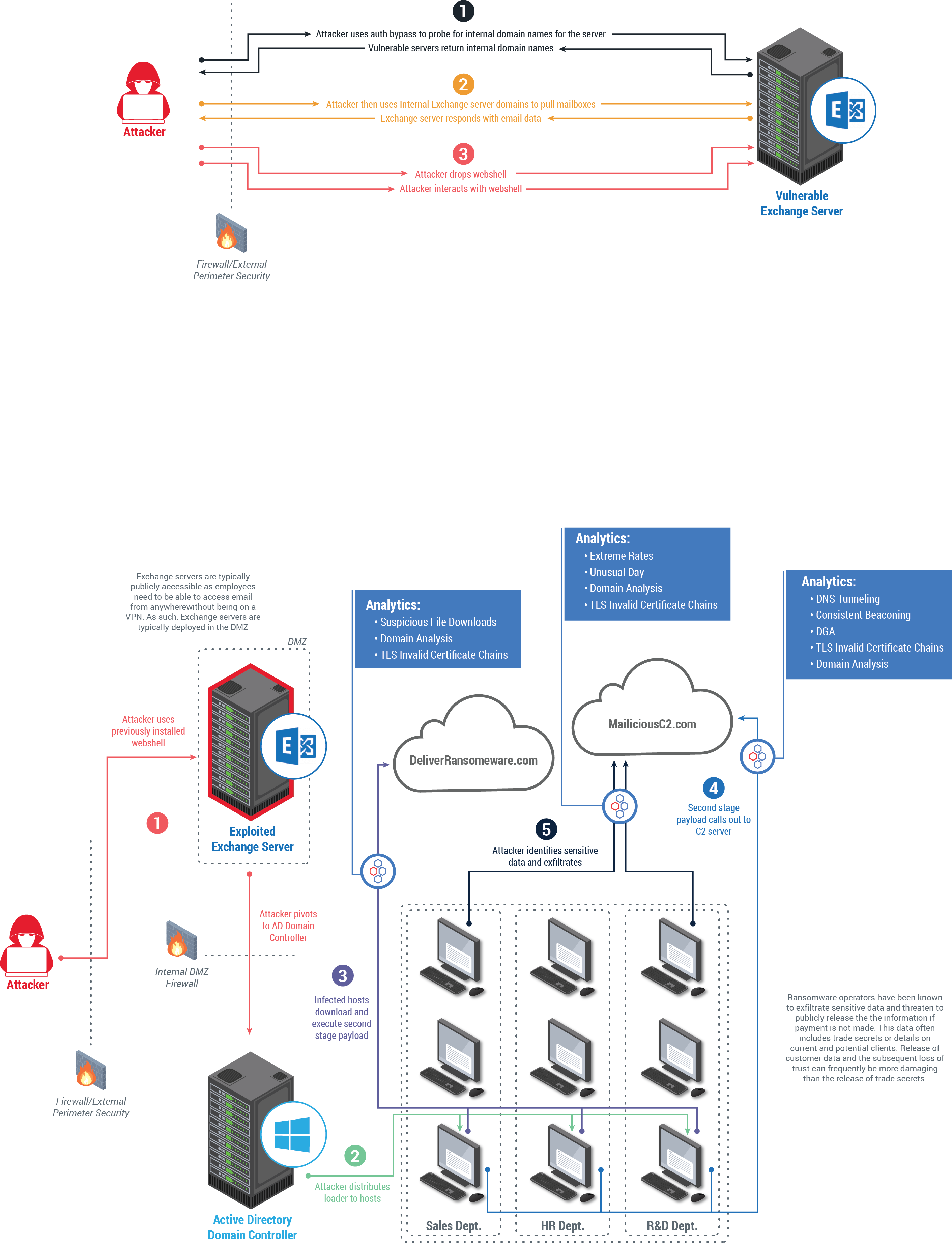
Microsoft on premise exchange hack. Essentially these hackers took three steps and exploited four separate vulnerabilities. Microsoft has released a new one-click mitigation tool Microsoft Exchange On-Premises Mitigation Tool to help customers who do. Security experts warn that any organization running on-premises Microsoft Exchange could be at risk for the Microsoft Exchange Hack.
Microsoft s Exchange mail servers have been targeted by a group of state-backed hackers operating out of China according to the tech giant. Several breaches of on-premises Microsoft Exchange Servers were observed by multiple players during the same month all of who alerted Microsoft. Microsoft has released a one-click mitigation tool as a stop-gap for IT admins who still need to apply security patches to protect their Exchange servers.
Based on these engagements we realized that there was a need for a simple easy to use automated solution that would meet the needs of customers using both current and out-of-support versions of on-premises Exchange Server. The Microsoft hack appears to have originated with the Hafnium organization out of China. Theres been a new ransomware attack on an on-premises Microsoft Exchange Server emphasizing once again the need for moving online.
The threat actors took advantage of. Heres how to find out if yours is one. Microsoft Exchange Hafnium Hack.
On 5 January 2021 security testing company DEVCORE researcher made the earliest known report of vulnerability to Microsoft. Exchange Server hack timeline January 3 2021. We strongly urge customers to immediately update systems.
In the attacks observed the threat actor used these vulnerabilities to access on-premises Exchange servers which enabled access to email accounts and allowed installation of additional malware to facilitate. New York CNN Business Many security experts remain alarmed about the large Chinese-linked hack of Microsofts Exchange email service a week after the attack was first reported. This was later verified by Microsoft on 8 January.
Microsoft said the Exchange flaws are being targeted by a previously unidentified Chinese hacking crew it dubbed Hafnium and said the group had been conducting targeted attacks on email systems. Recommended Steps March 10 2021 On March 2 2021 Microsoft Corporation announced that a well-organized China-based threat actor named Hafnium deployed targeted attacks against a number of US-based businesses currently hosting on-premise Exchange Servers using multiple previously-unknown zero-day. March 19 2021.
Adversaries are deploying DearCry ransomware on victim systems after hacking into on-premise Microsoft Exchange servers that remain unpatched Microsoft acknowledged late Thursday. MSPs That Did Not Move On-Premise Exchange To The Cloud Blew It In the wake of the disclosure that Chinese hackers had exploited several Microsoft Exchange on-prem. Hafnium gained access to Microsoft Exchange servers by taking advantage of stolen passwords and a previously.
The attackers then created a web shell or a backdoor that allows browser-based access to the. This guidance will help customers address threats taking advantage of the recently disclosed Microsoft Exchange Server on-premises vulnerabilities CVE-2021-26855 CVE-2021-26858 CVE-2021-26857 and CVE-2021-27065 which are being exploited. These flaws the company.
Cyber espionage operations against Microsoft Exchange Server begin using the Server-Side Request Forgery SSRF vulnerability CVE-2021-26855. They must take the threat seriously and follow the steps necessary to protect data assets. Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks.
Released on Monday the tool is designed.
 Microsoft Exchange Zero Day And Exploit Could Allow Anyone To Be An Admin Safe Program Zero Days Edifying
Microsoft Exchange Zero Day And Exploit Could Allow Anyone To Be An Admin Safe Program Zero Days Edifying
 What We Know So Far About The Microsoft Exchange Server Breach Pratum
What We Know So Far About The Microsoft Exchange Server Breach Pratum
 But Office 365 Is Just The Same As On Premises Functionality Office 365 Infographic Office 365 Sharepoint
But Office 365 Is Just The Same As On Premises Functionality Office 365 Infographic Office 365 Sharepoint
 Microsoft Releases Tool To Help Close Exchange Vulnerabilities Techzine Europe
Microsoft Releases Tool To Help Close Exchange Vulnerabilities Techzine Europe
 Newtechmalta Newtechmalta Twitter Office 365 Microsoft Exchange Server Business Analysis
Newtechmalta Newtechmalta Twitter Office 365 Microsoft Exchange Server Business Analysis
 Microsoft Chinese Hackers Are Exploiting Exchange Server Flaws To Steal Emails
Microsoft Chinese Hackers Are Exploiting Exchange Server Flaws To Steal Emails
 The Microsoft Exchange Hacks How They Started And Where We Are
The Microsoft Exchange Hacks How They Started And Where We Are
 Microsoft Releases One Click Exchange On Premises Mitigation Tool
Microsoft Releases One Click Exchange On Premises Mitigation Tool
 Gsx Monitor Analyzer Microsoft Exchange Hybrid Cloud Hybrid Cloud Gsx Operations Management
Gsx Monitor Analyzer Microsoft Exchange Hybrid Cloud Hybrid Cloud Gsx Operations Management
 Fully Protect Your Microsoft Exchange Server With Transientx Transientx
Fully Protect Your Microsoft Exchange Server With Transientx Transientx
 Microsoft Exchange Attack The Next Solarwinds
Microsoft Exchange Attack The Next Solarwinds
 Microsoft Exchange Targeted By China Linked Hackers It Pro
Microsoft Exchange Targeted By China Linked Hackers It Pro
 Organizations That Use The Microsoft Teams Chat Workspace Service But That Also Keep Their Exchange E Mail Server Data On Premises N News Apps Tech Updates App
Organizations That Use The Microsoft Teams Chat Workspace Service But That Also Keep Their Exchange E Mail Server Data On Premises N News Apps Tech Updates App
 Detecting Microsoft Exchange Vulnerabilities 0 8 Days Later Splunk
Detecting Microsoft Exchange Vulnerabilities 0 8 Days Later Splunk
 What S Going On With The Microsoft On Prem Exchange Hack Erp Software Blog
What S Going On With The Microsoft On Prem Exchange Hack Erp Software Blog
 Exchangerelayx An Ntlm Relay Tool To The Ews Endpoint For On Premise Exchange Servers Provides An Owa For Hackers
Exchangerelayx An Ntlm Relay Tool To The Ews Endpoint For On Premise Exchange Servers Provides An Owa For Hackers
 Microsoft Exchange Server Hafnium Zero Day Hack Swat Systems
Microsoft Exchange Server Hafnium Zero Day Hack Swat Systems
 Office 365 Message Attribution Messages Office 365 How To Apply
Office 365 Message Attribution Messages Office 365 How To Apply
 Microsoft Groups Demystified Successful Group Management Management Microsoft Success
Microsoft Groups Demystified Successful Group Management Management Microsoft Success
Post a Comment for "Microsoft On Premise Exchange Hack"