Microsoft Account Unsuccessful Login Attempts
When reviewing event id 411 specifically within the security logs of the ADFS servers you will note two IP addresses OriginIPAddressMicrosoftExchangeOnlineIP. If you see account activity that is sure it was you you can bookmark it on the recent activity page and we will help you protect your account.
 Believe It Or Not Microsoft S Mobile Strategy Is Still On Course Windows 10 Mobile Windows 10 Upgrade To Windows 10
Believe It Or Not Microsoft S Mobile Strategy Is Still On Course Windows 10 Mobile Windows 10 Upgrade To Windows 10
We have noted a drastic increase in the number of failed log on attempts coming from countries outside the US within ADFS obviously attempting to log in through Exchange Online.

Microsoft account unsuccessful login attempts. Hackers and others are being denied access to your account. Log in to the Security Basics page of your Microsoft account. My MS account is about as locked.
Event Viewer automatically tries to resolve SIDs and show the account name. If the password and the email from your MS Account were the same from those that you had on other websites this might me the reason of these unsuccessful sign-in attempts. Dont worry the sign-in attempt was unsuccessful but this bothers me that there are hackers out there attempting it.
Limit Failed Login Attempts Via the Command Prompt Open the Command Prompt by following these steps. Hi JaumeGT You can check the information in this article. Security ID Type SID.
Click Ctrl Shift Enter to open an elevated Command Prompt. The account locks again after each subsequent failed sign-in attempt for one minute at first and longer in subsequent attempts. Further incorrect sign-in attempts lock.
By default smart lockout locks the account from sign-in attempts for one minute after 10 failed attempts. SID of the account that was specified in the logon attempt. This post was originally published in.
Account For Which Logon Failed. In the article the user will be locked out for one minute after 10 unsuccessful sign-in attempts. MS shows a message for the entry.
All Microsoft account can be accessed online via https. Account lockout policy options disable accounts after a set number of failed logon attempts. We are all under constant attack All our accounts computers servers and connected devices are under constant attack.
If you get an email about unusual activity on your Microsoft account or if youre worried that someone else might have used your account go to the Recent activity pageYoull see when your Microsoft account was signed in during the last 30 days along with any device or app-specific info. Yes you can use AdminDroid Office 365 Reporter tool to monitor failed login attempts. Local Computer PolicyComputer ConfigurationWindows SettingsSecurity SettingsAccount Policies.
The favorite view available under User Activities Dashboard will clearly show daily failed login activities with the top user details. Go to Control Panel and click Internet Options and in General tab click Settings under Browsing History. The recent sign-on activities is just a record of failed login attempt caught by the security which you can replicate by intentionally setting up a failed IMAPPOP3SMTP access.
You can set a value from 1 through 999 failed sign-in attempts or you can specify that the account will never be locked by setting the value to 0. If Account lockout threshold is set to a number greater than zero Account lockout duration must be greater than or equal to the value of Reset account lockout counter after. Office 365 Password Policy.
Account lockout policy settings control the threshold for this response and what action to take after the threshold is reached. If the SID cannot be resolved you will see the source data in the event. Then click on View Files and do a search for Microsoft type Microsoft in the search box and delete all the Microsoft cookies found CtrlA then Del.
When we notice a sign-in attempt from a new location or device we help protect the account by sending you an email message. For information about specific settings see Password Policy. What happens if theres an unusual sign-in to your account Microsoft prioritizes account security and works to prevent people from signing in without your permission.
Press the Windows Key R and type CMD. You can find the demo of the dashboard here. Replied on April 5 2019.
A string of Unsuccessful sign-in entries failed login attempts are the system working as it should. The Windows and Windows Server operating systems can track logon attempts and you can configure the operating system to disable the account for a preset period of time after a specified number of failed attempts.

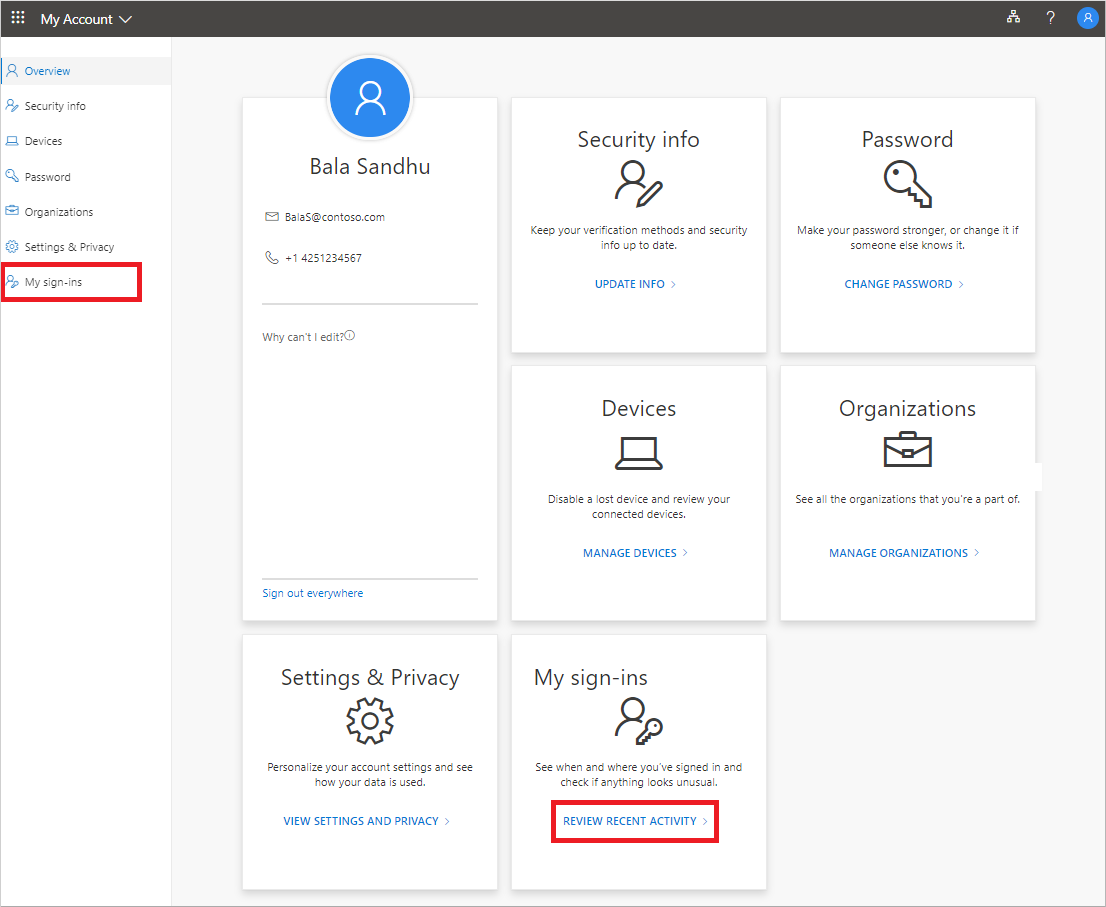 View And Search Your Recent Sign In Activity From The My Sign Ins Page Azure Active Directory Microsoft Docs
View And Search Your Recent Sign In Activity From The My Sign Ins Page Azure Active Directory Microsoft Docs


 Pin By Mounishree On Challenges Informative Interactive Windows
Pin By Mounishree On Challenges Informative Interactive Windows
 Mail Mathpbb7 Hotmail Com Writing Dialogue Prompts Book Writing Tips Story Writing Prompts
Mail Mathpbb7 Hotmail Com Writing Dialogue Prompts Book Writing Tips Story Writing Prompts
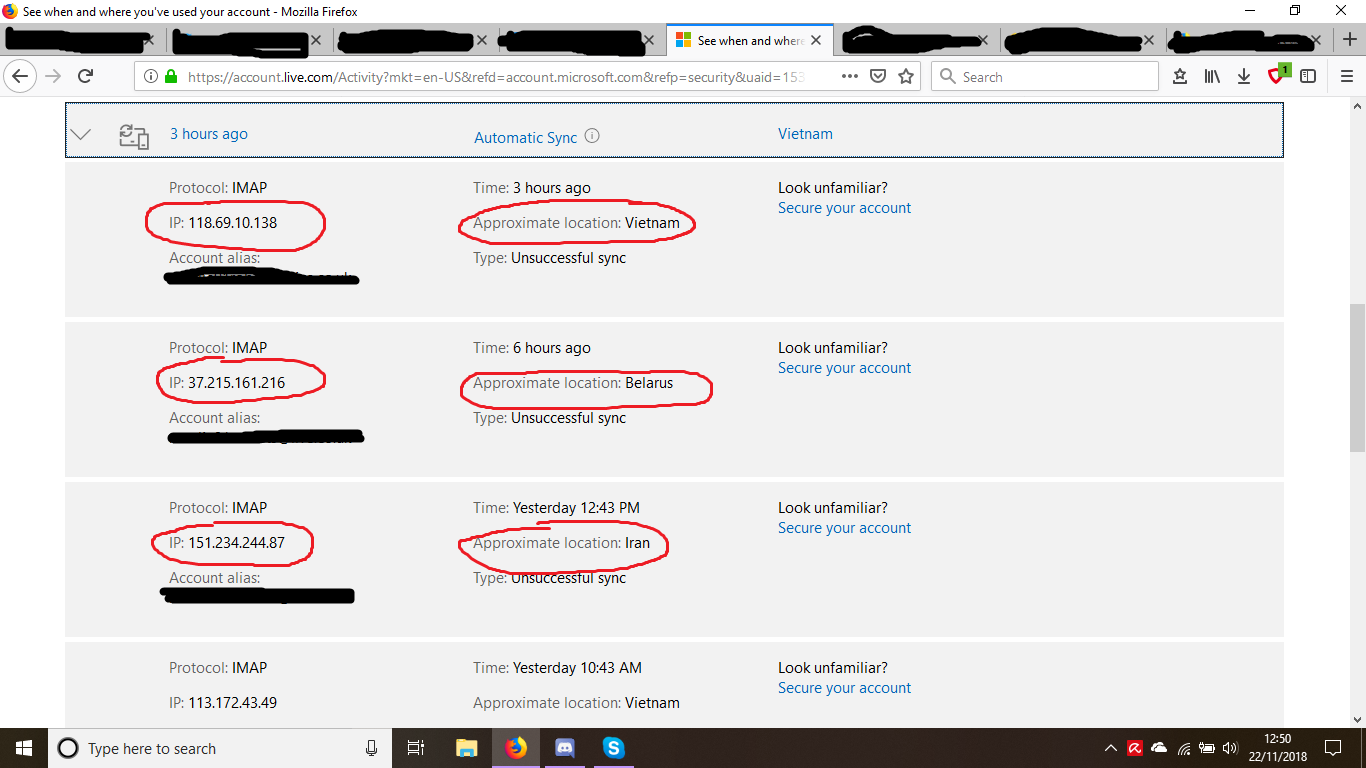
 Methods To Fix Microsoft Sql Server Error 983 Microsoft Sql Server Sql Server Microsoft
Methods To Fix Microsoft Sql Server Error 983 Microsoft Sql Server Sql Server Microsoft

 A2z Solutions How To Activate Ms Office 2010 2013 2016 Without A Ms Office Office Microsoft Office
A2z Solutions How To Activate Ms Office 2010 2013 2016 Without A Ms Office Office Microsoft Office
 New Office365 Alert Is A Phishing Attack Failure To Sync
New Office365 Alert Is A Phishing Attack Failure To Sync
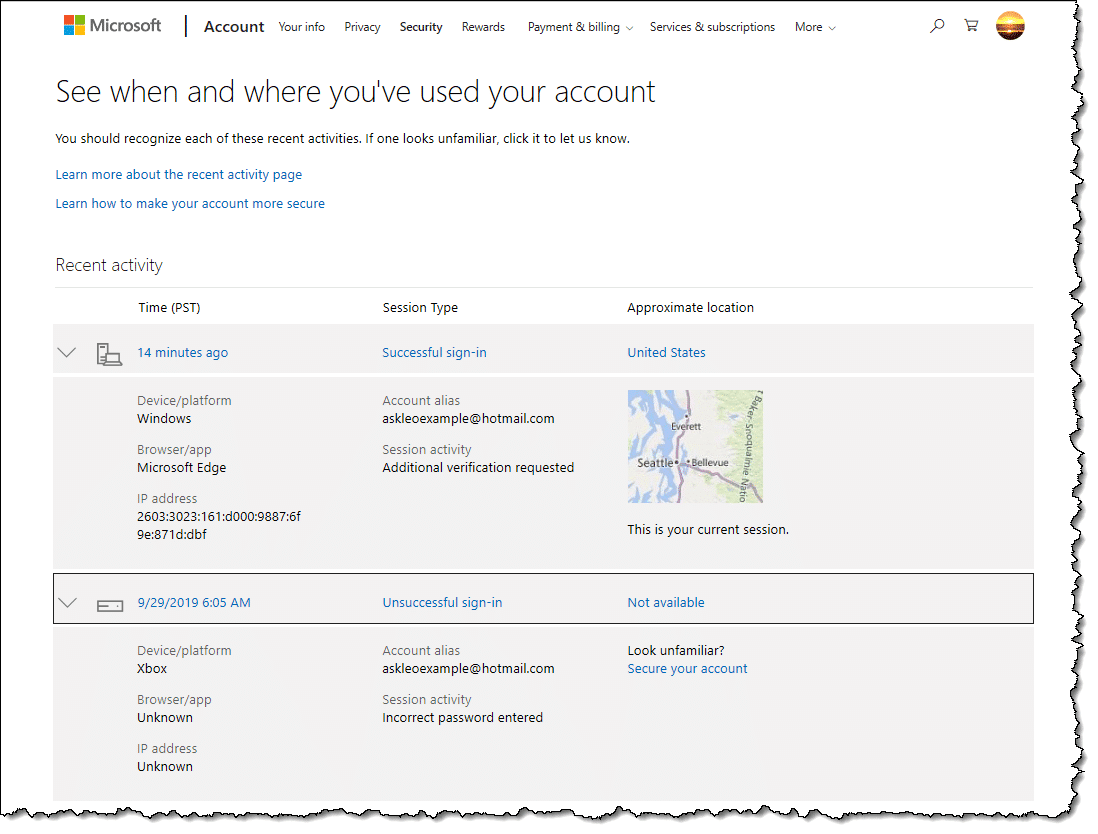 Why Do I See Lots Of Failed Login Attempts On My Account Ask Leo
Why Do I See Lots Of Failed Login Attempts On My Account Ask Leo
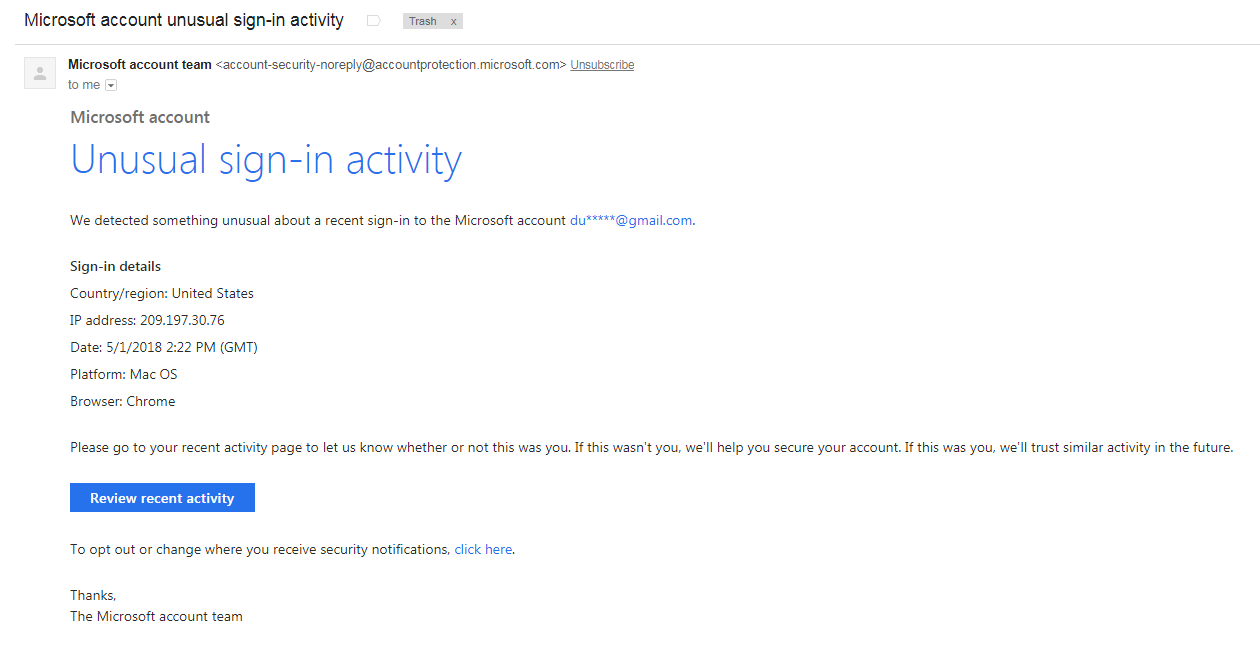 Unusual Sign In Activity On Microsoft Account What To Do
Unusual Sign In Activity On Microsoft Account What To Do
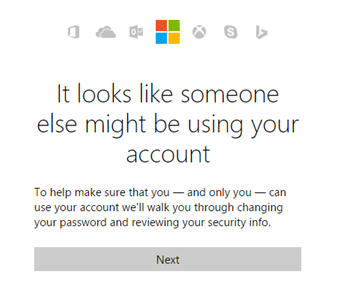 Unusual Sign In Activity On Microsoft Account What To Do
Unusual Sign In Activity On Microsoft Account What To Do
 Recover A Microsoft Account Password 4sysops
Recover A Microsoft Account Password 4sysops
 Possible Hacked Microsoft Email Account Solved Windows 10 Forums
Possible Hacked Microsoft Email Account Solved Windows 10 Forums
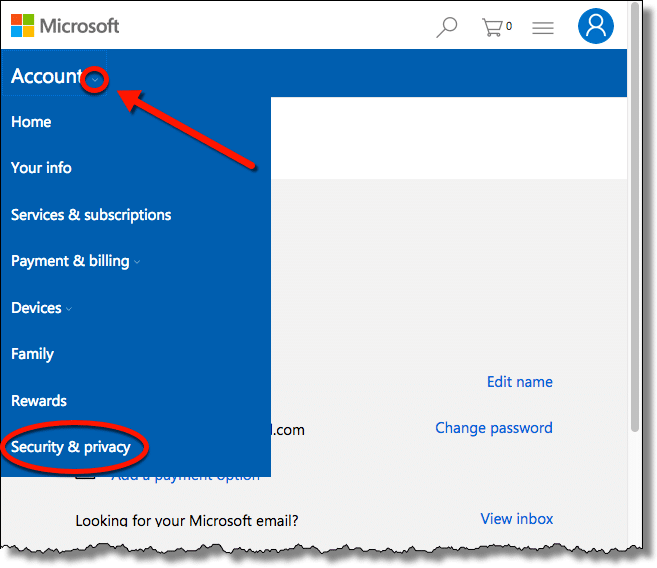 Recover Your Microsoft Account Later By Setting Up A Recovery Code Now Step By Step Instructions Ask Leo
Recover Your Microsoft Account Later By Setting Up A Recovery Code Now Step By Step Instructions Ask Leo

Post a Comment for "Microsoft Account Unsuccessful Login Attempts"